3CX, a leading communications software company, falls victim to a North Korean state-sponsored hacking group, through a software supply chain attack via a now-defunct online trading platform.
It would seem far-fetched if it weren’t becoming all too commonplace in this day and age, with these types of attacks remaining a persistent threat to organisations.
But what exactly happened?
And what did it mean for other businesses, let alone those using 3CX?
Initial 3CX Security Breach
On March 29th 2023, 3CX received reports of a malicious actor exploiting a vulnerability in their product.
Immediately, 3CX enlisted the help of Mandiant, a company specialising in cyber defence, threat intelligence, and incident response services.
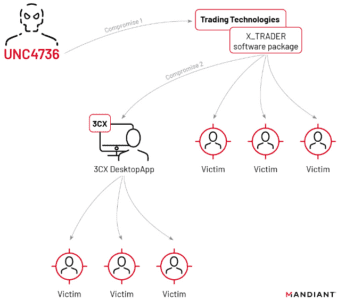
Their initial investigation suggested a highly experienced hacker was behind the attack, compromising 3CX’s network via malicious software downloaded from the Trading Technologies website.
“We regret to inform you that our company has become victim to an[sic] attack on our product and the larger supply chain. Our highest priority is to be transparent in sharing details on what actions we are taking in response to this incident and what we know to date. Information is rapidly unfolding in this ongoing investigation.”
3CX CEO Nick Galea, April 1st 2023
How it happened
The 3CX breach began when an employee unknowingly installed malware-laced software onto their personal computer.
The installer for X_Trader, a software package from the Trading Technologies website, had been compromised in an earlier attack on the software supply chain, by malware called VEILEDSIGNAL.
VEILEDSIGNAL had the ability to gain administrator privileges on the computer, thus stealing the employee’s 3CX credentials.
The threat actor then began to move laterally through the 3CX system, which means that they could move deeper into the system using certain tools and existing information on the device, remaining undetected while obtaining information and increased access.
The attacker was then able to compromise both the Windows and macOS 3CX desktop applications, allowing the threat actor the ability to download and run code on all machines where the app was installed.
Credit: Mandiant
Incident Response
This is the first time Mandiant has seen a software supply chain attack follow on from another software supply chain attack, and while their investigation has been able to pinpoint the origin and development of the attack, the full extent remains unknown.
However, 3CX having caught on to the breach within weeks as opposed to months, (which has been the case in other high profile supply chain breaches), seems to have limited the impact from the attack on 3CX and its end customers.
“The identified software supply chain compromise is the first we are aware of which has led to a cascading software supply chain compromise. It shows the potential reach of this type of compromise, particularly when a threat actor can chain intrusions as demonstrated in this investigation.”
Mandiant, April 27th, 2023
Mandiant’s report concluded that the 3CX attack was orchestrated by UNC4736, a North Korean state-sponsored hacking group possibly involved in financially-motivated cybercrime operations.
A “Cautionary Tale of Success”
Due to the swift action of 3CX, its transparency throughout the ordeal and its collaboration with private cyber security companies and the U.S. Government, 3CX is being commended, rather than condemned, for its response to the breach.
Within a day of being detected the command and control infrastructure of the hackers was dismantled by endpoint security companies such as CrowdStrike, SentinelOne, and others.
CrowdStrike’s senior vice president Adam Meyers has been quoted as saying “Right now, I think it’s a cautionary tale of success. I wouldn’t say that there’s no worry, but that [the supply-chain] aspect of the operation has been largely exposed and is in the process of being remediated.”
Thanks to the coordinated response from both industry and government, the damage from this particular incident is far less than what would be expected considering the extent of the breach.
However, what this breach has highlighted is the potential for lateral movement not only between private users and organisations, but between organisations and each other, which could no doubt have catastrophic consequences.

The Aftermath
In the wake of the breach, 3CX has since advised users to:
- Uninstall the 3CX Electron Desktop App from all Windows and Mac devices.
- Continue AV scans and EDR solutions in your organisation’s networks for any potential malware with the latest signatures.
- Switch to using the PWA Web Client App instead of the Desktop App.
They have also extended customers’ subscriptions by 3 months free of charge, are providing a dedicated support forum and free help tickets, and are continuing to provide updates through their social media and RSS feed.
Looking to the future
While it’s true that no system can ever be truly safe from malicious hackers, 3CX has announced a seven step security plan to drastically reduce the chances of an attack on this scale ever happening again.
“Following our Security Incident we’ve decided to make an update focusing entirely on security.”
3CX CEO Nick Galea, April 11th, 2023
Some of these measures have already been implemented, while others are being worked on and will be coming very soon.
Here’s an overview of the entire plan.
- Strengthening Network Security
Increased security for 3CX is being implemented through various means, such as:
- A rebuild that will make it harder for hackers to break into the network
- New Endpoint Detection and Response tools (EDR), EDR tools monitor devices to prevent cyber threats from breaching
- 24/7 offsite monitoring by cyber attack specialists
- Increased scrutiny with access control
- Remediation plan actions, this is designed to help ‘clean up’ after the attack and put measures in place to prevent this occurring in the future
- Increasing Software Security
To ensure that the software on 3CX’s downloads server is safe, code monitoring and analysis will take place to ensure there are no weaknesses that can be exploited.
- Ensuring Products are Secure
3CX is currently working with Mandiant, one of the world’s premier cybersecurity firms, to identify and patch any vulnerabilities in the many different products 3CX is responsible for.
- Improving Product Security
As part of the recently released update 7A, 3CX is protecting its users by implementing features such as password hashing. This means your password is converted into a string that is impossible to revert, preventing hackers from obtaining it. On top of this, numerous exploits have been fixed.
- Fake Cyberattacks
Penetration testing will be coming in the near future, this where a simulated and harmless cyber attack is performed on 3CX with the intention of gauging its security and detecting vulnerabilities ahead of time.
- Communication and Crisis Management Plans
As well as informing users of plans moving forward through blogs and social media, 3CX is also in the process of forming a crisis management and alert handling plans to be better prepared if an attack occurs in the future.
- Network Operations and Security
A new department has been announced to help 3CX make the best decisions in improving the network operations and security. A substantial budget is planned for this department, which will help ensure that only the greatest security measures will be undertaken.

What this means for customers.
This security incident has only served to drive 3CX to provide a safer, more secure service, and maintain transparency and competence in the face of a nation-state threat actor.
The X_Trader software supply chain attack affected more organisations than 3CX, and yet it is 3CX who have led the way in the discovery and resolution of this incident, which is why their breach has been so newsworthy.
The threat now is less about what happened to 3CX and more about the potential for far greater damage.
What other companies have undetected attackers lurking at present? How can we protect individuals and organisations from transferring malicious software?
How can we prevent concealed lateral movement which allows threat actors to access multiple organisations at once?
How do we protect vendor-customer relationships and the supply chain across the board?
While there are plenty of questions and possibilities as a result of this incident, we are very thankful that not one of our clients has been affected.
We are available at any time for questions, either from our existing clients or those who are simply curious.
Since the attack, some threat researchers have put together a tool to help identify victims, but if you have any questions or queries, please do not hesitate to contact us.


